Sextortion: Five Ways Predators Blackmail Kids
Protect your children from sextortion scams
MAY 18, 2022
Sextortion: Five Ways Predators Blackmail Kids
Protect your children from sextortion scams
Sextortion is a crime where the perpetrator obtains compromising photos or videos from a victim and then uses those materials to blackmail them into sending money, more images, or performing sexual acts.
This crime usually occurs after a victim willingly provides sexual images to a friend or romantic partner, but some victims are being blackmailed online by strangers.
Often, these online predators obtain compromising images through fraudulent means. In 22% of all sextortion cases, the perpetrator acquired sexual images by deceit or without the victim’s consent.[5]
Children are particularly vulnerable to sextortion scams.
One in five sextortionists acquire sexual images through deceptive or fraudulent means.
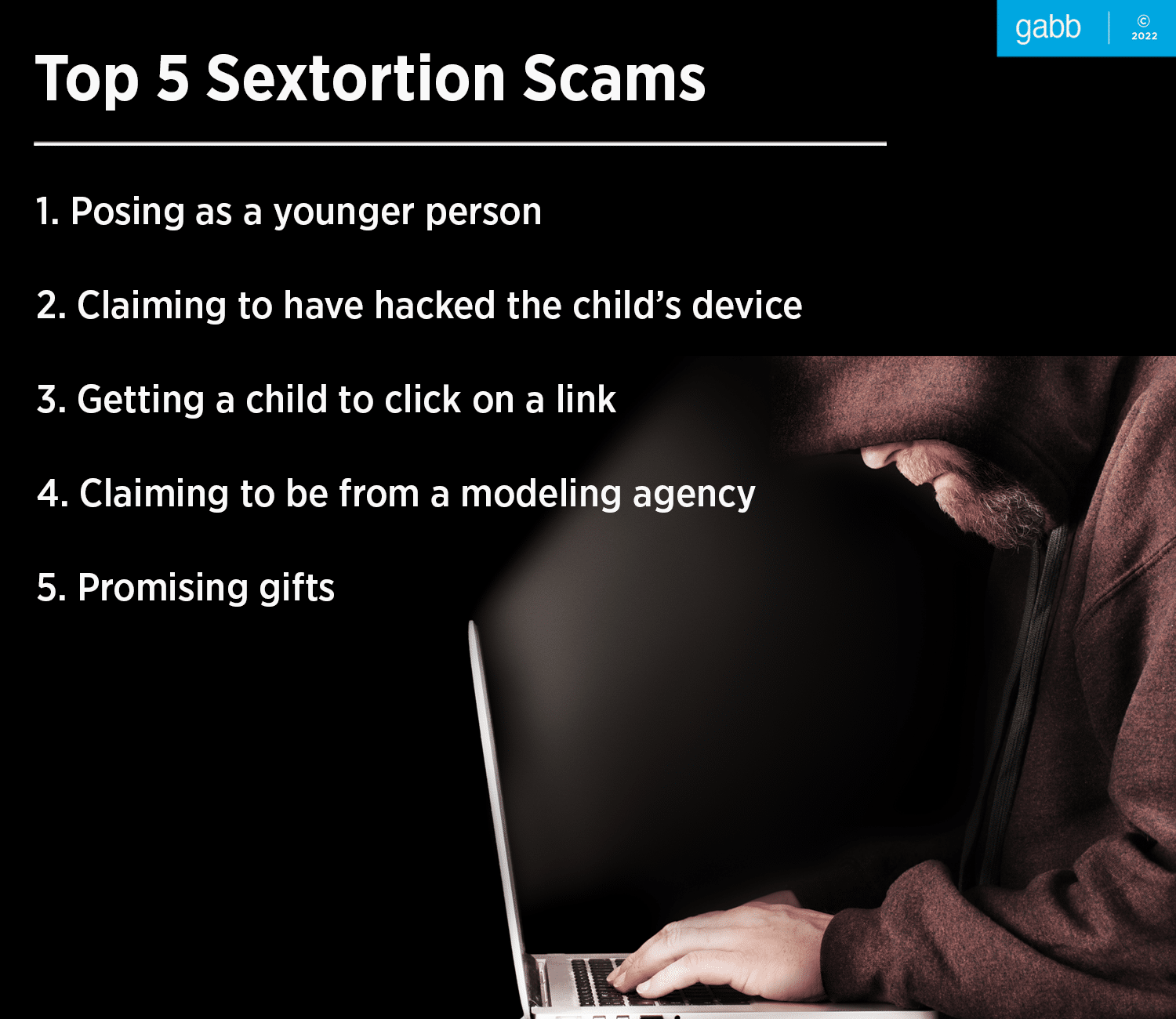
Five Ways Predators Blackmail Kids
Although internet predators are constantly developing new ways to exploit children, recognizing common tactics is an important defense against falling victim to sextortion schemes.
Knowing a few of these, parents can help their children recognize threats and teach them how to spot common sextortion scams.

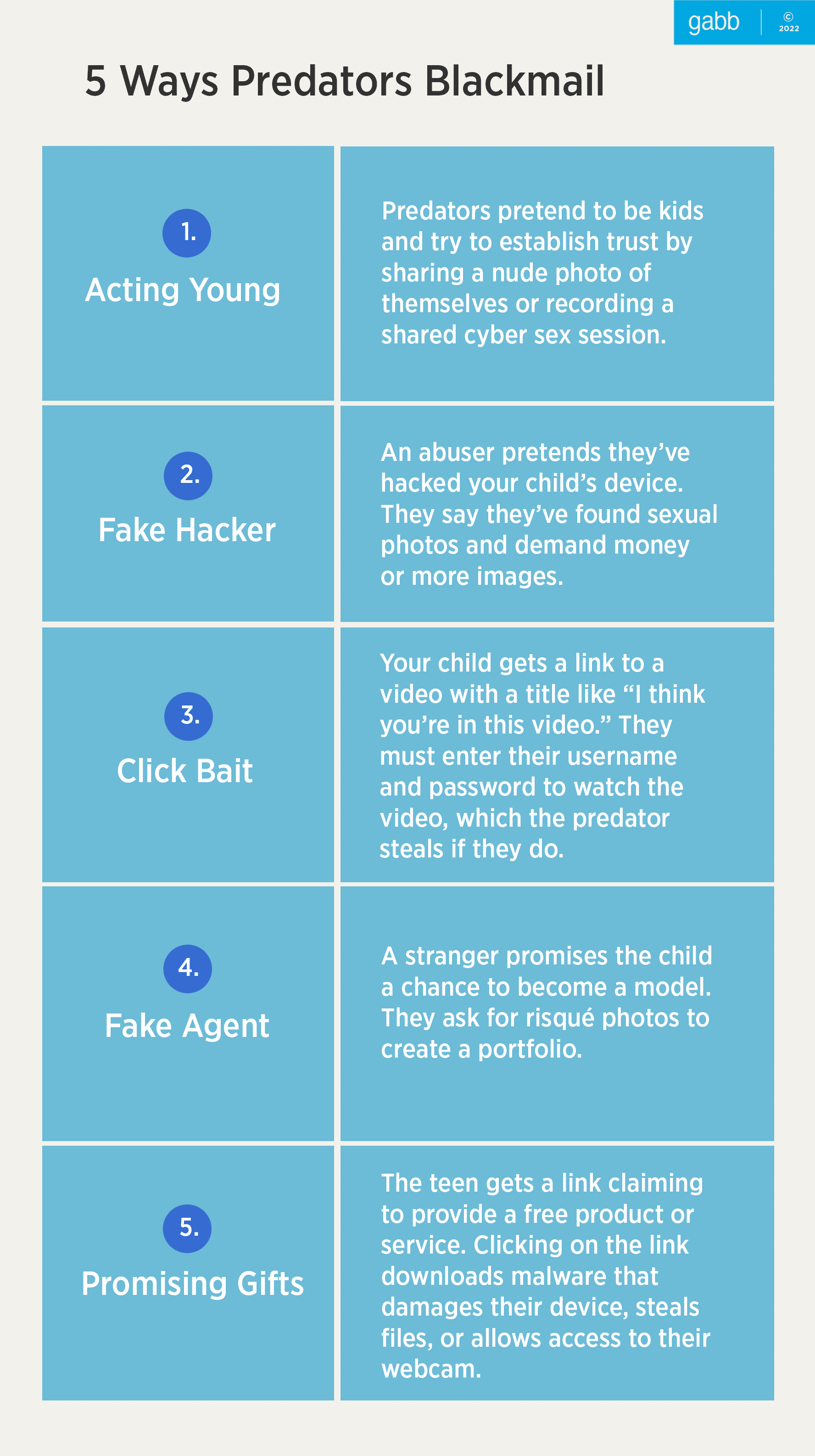
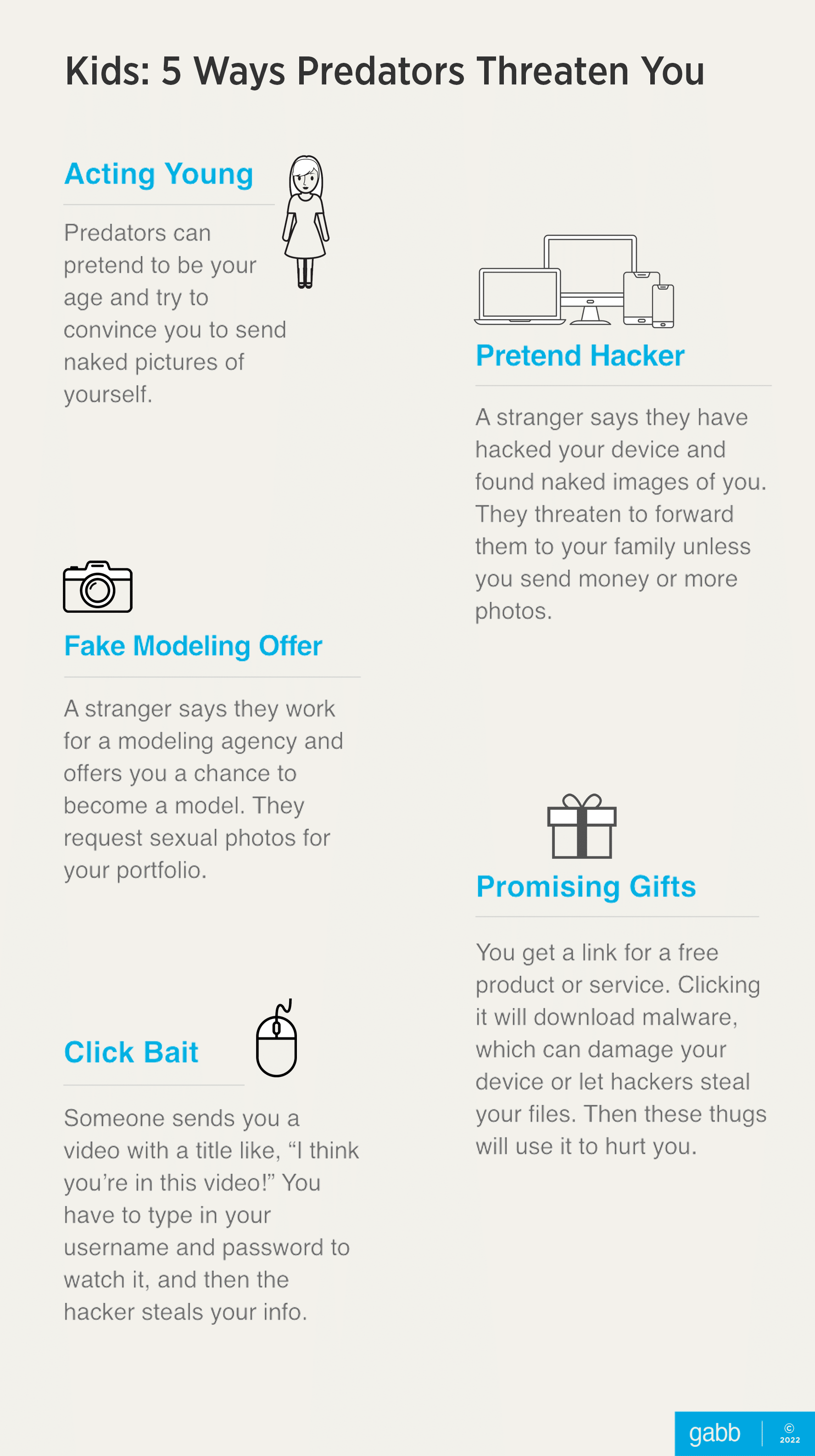
1. Posing as a younger person
A predator will pose as a young person the same age or slightly older than their target. They flirt a bit and then manipulate the child by sending nude “selfies” and asking for some back.
It is common to pressure the child to engage in cyber sex and secretly record it. This strategy is especially effective against boys because many young men don’t think sextortion can happen to them.[2]
Children can avoid falling prey to this tactic by learning to never send nude or sexual images and videos of themselves to anyone—friend, acquaintance, or stranger. Parents can help their children understand the concept of digital permanence: that an image shared online lasts forever.

2. Claiming to have hacked the child’s device
Abusers will claim to have hacked a young person’s computer or phone and convince them they have compromising material, such as sexual photos.[3]
The perpetrator will often include the child’s password as “evidence” of their hack in the threat.
Children are typically unaware that sextortionists can obtain passwords from data breaches, so if they have compromising materials, they will send that instead of the password as evidence.
When a kid sees their own password in a message from a stranger, it is disconcerting and can throw them off balance. The perpetrator uses this opportunity to pressure the child into sending actual photos, which they can then use for further acts of sextortion.
Responding to this type of situation requires children to have the right skills. If they receive a request, they can learn to never reply and bring their device to a trusted adult. Caregivers and parents can screenshot the message and then report the incident to authorities, including school administrators as warranted.

3. Getting a child to click on a link
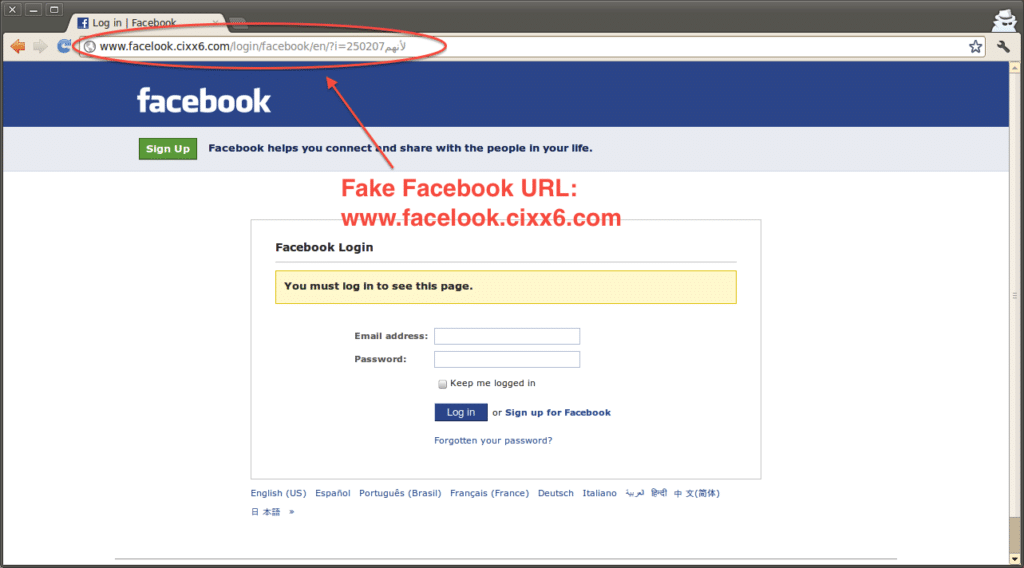
A “friend” will send the adolescent a link to a video with a title like “I think you’re in this video!” or “I can’t believe you did this!” over social media. Clicking on the video takes them to a legitimate-looking login page requesting their username and password before they can view the content.
The page is a dummy site, usually a blank page. Now, the hacker has their information and can access their account, looking for private messages, pictures, and other potentially compromising content.
Children need to be taught to be suspicious of any link that asks them for personal information. By looking at the URL, they can tell when a website is posing as their favorite social media site. These fake sites have sketchy URLs and just feel off.
For example, consider the following screengrab. This link has taken the user to what looks like a legitimate Facebook login page. Notice the strange URL consisting of random letters and numbers.
Consider sharing this with your child and roleplaying what they would do if they received a link similar to the one described above.
4. Claiming to be from a modeling agency
An enthusiastic person contacts a child and claims to work at a modeling agency. The blackmailer promises the young person money, an opportunity to get into the industry, or the chance of becoming famous.
In order to build a portfolio, the perpetrator will then ask for a few risqué pictures of the child or will edit the images to make them sexually explicit. Children are at a time in their development where most look for outside affirmations that they are attractive and so this tactic makes kids particularly vulnerable.
Parents can create a protective boundary for their family by teaching children to be cautious and intentional about what pictures and personal information they send to others or post online. If anyone they don’t know approaches them online asking for images of themselves, they should tell a trusted adult.
Parents can also strongly encourage their children to make their social media accounts private.

5. Promising gifts
The young person will get an email, social media message, or text offering them free products or services. This could be a music download, pornography, a popular computer game, a program that will enhance their social media presence, or anything else that might pique their interest.
Clicking on the link then downloads malware. Predators are even brazen enough to send packages to the child’s school or home.
This malware might damage their device, steal files, track keystrokes and mouse movements, or even allow the hacker to access their camera without them knowing it.
What Parents Can Do
Sextortionists, like all online predators, are conniving. They are constantly creating new schemes to trap unsuspecting victims. While there is no way we can always know about every possible scam, there are a few general guidelines we can teach our children to help them stay safe.[2]
Safe tech enables kids to stay connected without the risks associated with smartphones, such as bad actors, smartphone addictions, and other risks related to technology.
Parents can also consider using safe devices for their families. Safe tech is not connected to the internet and fosters learning tech in steps. Safe tech provides kids a way to stay connected, but unlike a smartphone, they are protected from bad actors, smartphone addictions, and other technology-related risks.

Protection Against Other Forms of Sextortion
While parents and teens should be aware of these potential sextortion scams, the majority of sextortion threats come from people kids know.
Nearly three-quarters of sextortion victims are threatened by a former dating partner, friend, or other person they know well. In these instances, the victim isn’t tricked into it, but willingly provides sexual images when they are in the relationship.[4]
With awareness and education, there is always hope. Read this article from Stop Sextortion to learn more about what sextortion is, appropriate next steps, and how to protect your family.













Success!
Your comment has been submitted for review! We will notify you when it has been approved and posted!
Thank you!